Secure workloads across cloud, save costs, and stay assured
Businesses today are pursuing newer ways to accelerate innovation and collaboration in this fast-paced digital era. And they seem to have found solace in cloud computing, which plays a significant role in growing businesses. Organizations host much of their data and applications in the cloud. But this cloud data is not entirely safe and is prone to insider attacks just like cyber-attacks. Security threats are continuously evolving and becoming more sophisticated. So, securing the cloud environments against unauthorized access to data, attacks, hackers, malware, and other risks is the need of the hour. A well-designed cloud security approach can significantly trim down the risk of attacks in the cloud.
Cloud security, also known as cloud computing security, refers to strategies, procedures, and technologies that work collectively to protect cloud-based infrastructure. These security measures are configured to protect cloud data (from theft, leakage, corruption, deletion), cloud computing environments and support regulatory compliance. These measures also ensure setting authentication rules for individual users and devices, thus protecting the customer’s privacy.
Importance of cloud security for businesses
Cloud computing and cloud security go hand in hand. Cloud computing, which refers to the delivery of information technology services over the internet, has become a must for businesses in the virtual world. Using cloud computing, organizations can operate at scale, shrink technology costs, and use responsive systems that enable them to get a competitive edge. Organizations realize many business benefits of moving their devices, data centers, business processes, applications, and procedures to the cloud. They are pursuing the best methods to secure their business data, thereby making cloud security imperative.
All cloud models are susceptible to threats making it essential to have the proper security provisions in place, irrespective of businesses running on the native, hybrid, or on-premise environment. Cloud security comes with the added advantage that it can be configured and managed to the business’s exact needs, reducing administration overheads and facilitating IT teams to focus on their work areas. It is thus necessary for companies to work with a cloud provider that can provide custom-made security.
Let us now explore the many benefits that Cloud security offers–
- Centralized security – centralized system for the protection
- Reduced costs – with the elimination of dedicated hardware costs and fewer customer care executives
- Reduced administration – with eliminating the need for manual security configurations and constant security updates
- Reliability –allows safe access to cloud data and applications across any location or device
- Firewalls –protects the network security, end-users, and traffic between different apps stored in the cloud
- Access Controls- allows setting access permissions to protect cloud data
- Data Masking –maintains data integrity by keeping crucial information confidentia
- Threat intelligence– helps protect mission-critical assets from threats
- Disaster recovery – helps to recover data that is lost or stolen
- Enhanced protection– that works 24/7
How does the cloud security actually work?
Organizations and the cloud service providers work together with a shared responsibility to implement the right security controls needed to protect the applications and data that are stored or deployed in the cloud. To understand cloud security working, let us learn about cloud computing security controls and cloud environments.
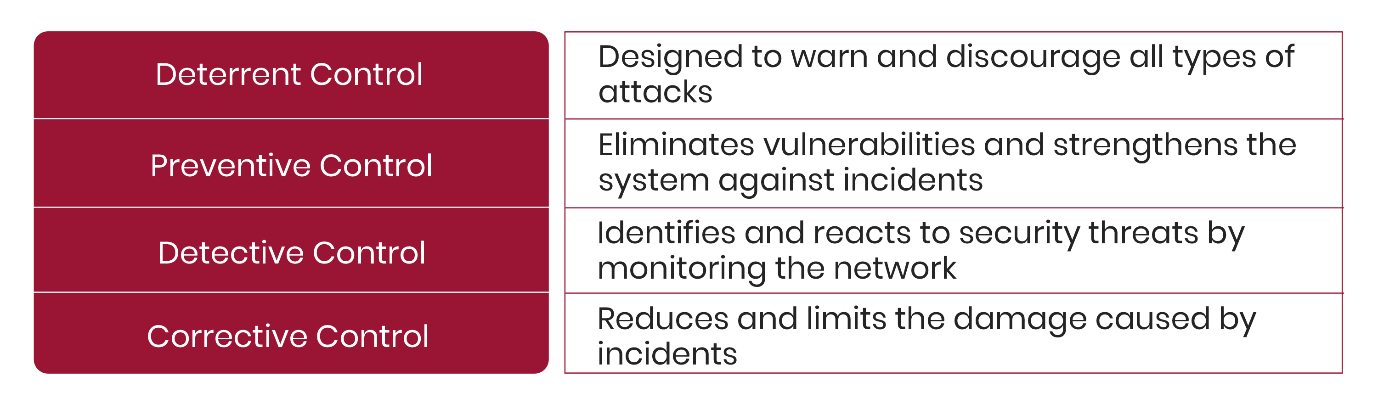
The cloud computing security controls incorporate safety measures to reduce and eliminate different types of risks, like- the creation of data recovery, business continuity plans, encryption of data, and monitoring access to the cloud. An alert security operations team applies appropriate procedures to prevent and control the impact of any attack. Each type of security control is significant in providing stability to the cloud environment.
Cloud computing security controls
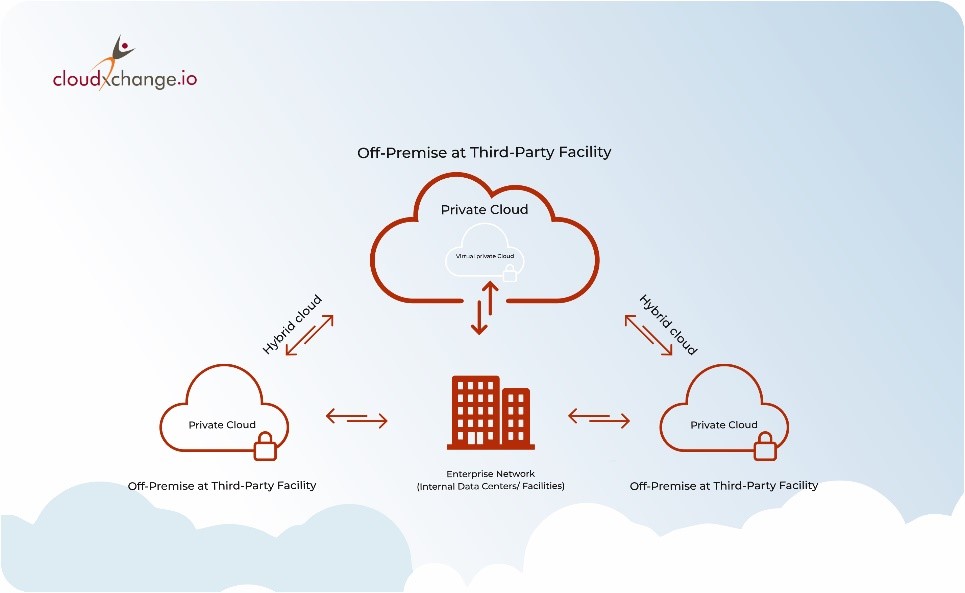
Cloud Environments and cloud security responsibilities
There are mainly 3 cloud environments-
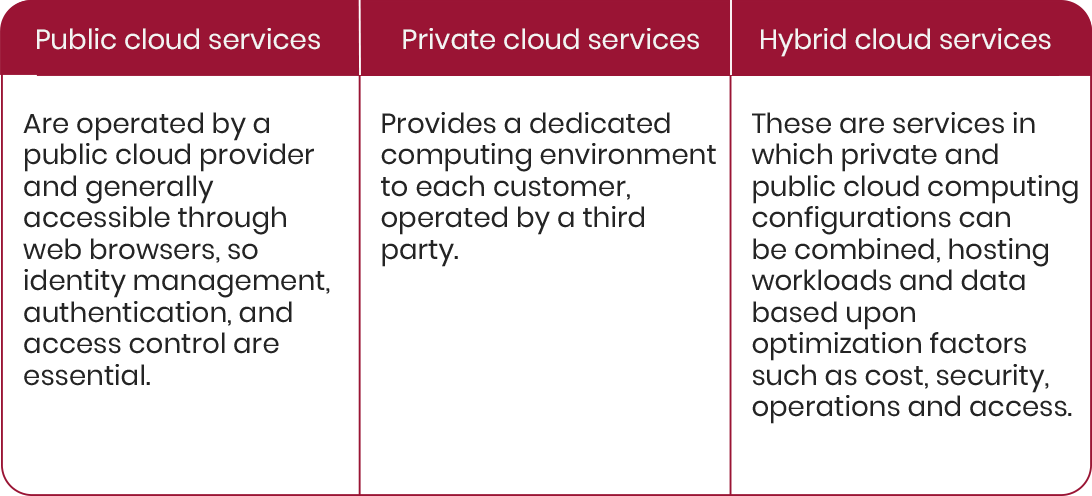
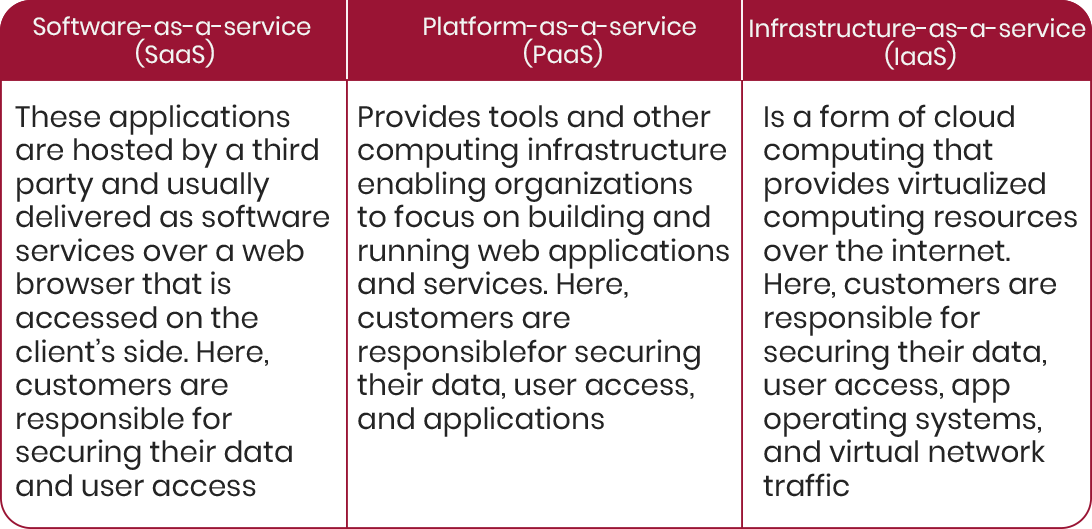
Cloud service models involve both the cloud provider and cloud customer, where both share different levels of responsibility for security. By service type, these are:
cloudxchange.io helps accelerate businesses
The security model from cloudxchange.io exhibits a distinct ability to progress and keeps business data secure and compliant. It is a complete cloud security solution that protects cloud apps and cloud data by preventing unauthorized access. Get benefitted by –
- Reduced risk with deeply integrated services improved privacy and data security
- Grow enterprise-wide with higher visibility and control
- Gain wide-ranging security and compliance Controls
Cloud computing and cloud security involve risk; hence it is essential to work with a cloud service provider that offers best-in-class security that has been customized for your infrastructure. Businesses need to select the right cloud security solution to protect their organization from unauthorized access, data breaches, and other threats.